Cloud application security is indispensable to the protection of applications and other critical digital assets in the contemporary cloud-based technology landscape. With the escalating adoption of cloud technologies, its significance has continued to grow, especially in the areas of threat detection and response and data protection.
According to IT Governance, 35,900,145,035 known records have been breached so far in 9,478 publicly disclosed incidents in 2024.
What is Cloud Application Security?
It is the practice of safeguarding applications (and data) in collaborative cloud environments. It is a system of technologies, tools, policies, processes, rules, controls, and even people that enable organizations to secure their cloud-based software applications. It has become a must for organizations looking to protect their cloud applications from the increasingly sophisticated attacks and widening range of threats within the cloud environment.
It is crucial for enterprises to have a robust and foolproof cloud application security strategy in place. This helps improve the cloud security posture, mitigate security risks, thwart emerging threats and cyberattacks, avoid business disruption, and confidently, safely leverage the cloud.
Recently, Harbinger conducted a Power Hour on ‘Tips to Protect Cloud Applications from Emerging Security Threats’ where industry experts shared their insights and knowledge on improving cloud security. This interactive session was hosted by Harbinger President and CTO, Shrikant Pattathil. It featured Sandeep Angra, Chief Information and Technology Officer, Unifi and Sachin Suryawanshi, Software Architect, Harbinger Group as panelists.
Cloud Application Security Tips to Implement Right Now
When it comes to protecting your cloud applications from security threats, it is not ideal to seek a silver bullet as the initial approach. You need to have a comprehensive, detailed, and targeted approach to safeguard your cloud applications and infrastructure from emerging security threats.
Here are some cloud application security tips you can start implementing in your organization.
Tip #1: Plan the right enterprise and cloud security investment and get a buy-in from the C-Suite and leadership team for that investment.
Tip #2: Make it a priority to set up the right cloud application security team, including talented engineers, and an experienced CISO to lead them.
Tip #3: Create awareness about enterprise and cloud security within your organization. Ensure the people in your organization are aware of the different types of security threats and attacks that exist, such as phishing, brute force, DDoS, malware, and account takeover. This awareness needs to be directed upward and downward in your organization.
Upward Awareness: Educate your organization’s leadership about the criticality of cloud security threats and significance of establishing a secured cloud environment. Inform the team about the kinds of cloud security threats your organization is currently facing or could face in the future. Explain the specific measures and investments required to avoid and mitigate cloud security risks.
Downward Awareness: Have a continuous and consistent dialogue with the employees in your organization to increase awareness about cloud application security. Use emailers, nudge-learning, gamification, video-based online courses with assessments, or conduct live sessions and webinars to raise awareness. Make employees aware of the actionable steps and preventive measures they need to take to ensure the enterprise and cloud application security of your organizations remains intact.
Tip #4: As a CISO or CIO, you need to learn to trust your gut and take appropriate action if you sense a threat to cloud application security.
Learn how Harbinger helped a High-Tech company efficiently manage cloud infrastructure monitoring. We reduced the response time to alerts by 30%.
Tip #5: Keep security at the forefront of your cloud application design and development rather than having it as an afterthought. Take a “shift left” approach to security to solidify your cloud application security. The shift left security practice helps identify coding errors and vulnerabilities much earlier in the software development life cycle (SDLC).
Here are some shift left security best practices:
- Evaluate your existing software development process, how your development pipeline functions, and how the code progresses from development to production.
- Create a new shift left security strategy which includes your objectives of adopting the shift left approach, how you define shift left and the supporting tools and processes, success measurement, and team roles and responsibilities.
- Provide shift left security training to your developers and other teams like QA and product. Educate them on secure coding best practices and standards.
- Prepare for shift left security by automating security processes. Runtime Application Self Protection (RASP), Interactive Application Security Testing (IAST), Dynamic Application Security Testing (DAST), and most applicably, Static Application System Testing (SAST) are powerful approaches to security automation. For better cloud application security results, you can shift left in DevSecOps or take the newest approach “Shift Everywhere + DevSecOps.”
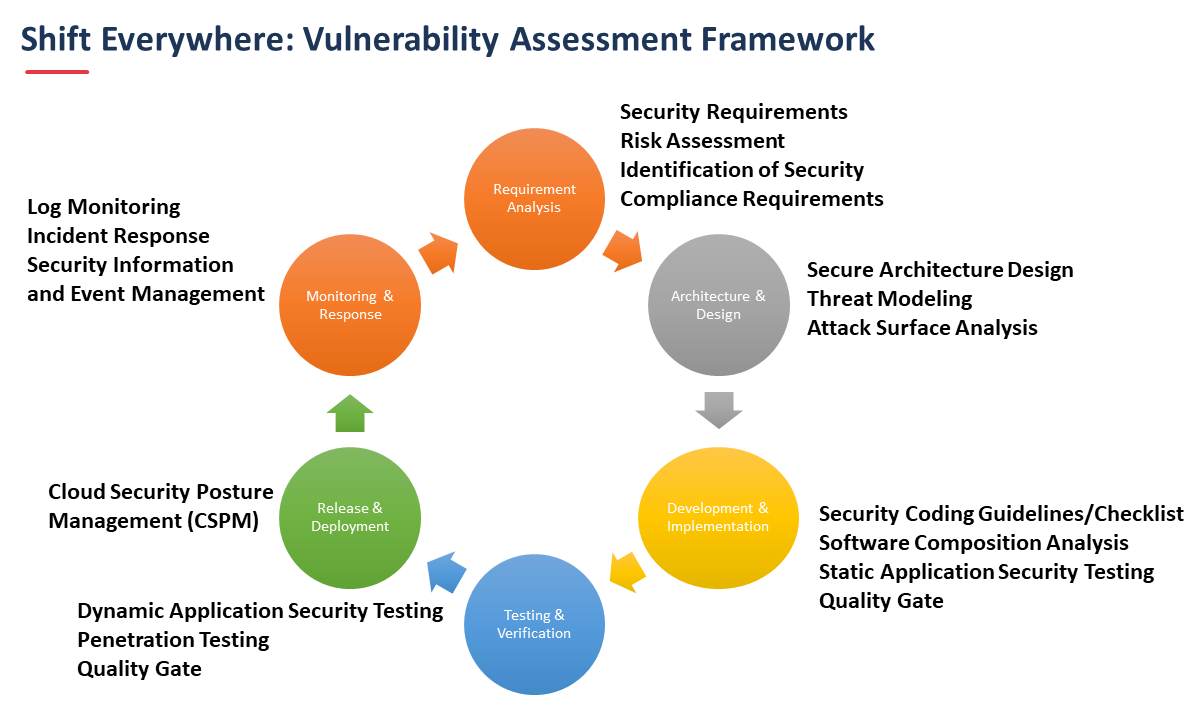
Tip #6: Conduct independent security assessment and vulnerability testing monthly or weekly. Having an outsider’s eye to assess your cloud application security and enterprise IT infrastructure security is essential. Independent security assessment helps identify missed gaps in your cloud application security. Experts say that a secure code released today may not be secure tomorrow.
Tip #7: Leverage advanced threat detection solutions to strengthen your cloud application security. Have clear and effective security policies in place, along with good governance to ensure improved cloud security and be in a better position to identify and eliminate vulnerabilities.
Take Action to Protect Your Cloud Applications and Infrastructure
Safeguarding your applications and data in the cloud requires a proactive approach. Implementing robust security measures, such as Shift Everywhere + DevSecOps, access controls, vulnerability testing, and regular audits, is paramount to mitigate cloud security risks. Additionally, staying informed about emerging threats and keeping your systems updated help ensure ongoing protection.
Remember, cloud application security is a shared responsibility between your users, employees, cloud security team, and cloud service provider. By prioritizing vigilance and adopting a multi-layered defense strategy, you can fortify your cloud environment against potential breaches, attacks, and unauthorized access.
Embrace the tips shared above to bolster your cloud security posture and protect your valuable digital assets in an ever-evolving cloud landscape. If you would like to learn more about cloud application security or need advanced cloud engineering services, reach out to us today.