IT security has always been a burning issue on the chief information officer’s (CIO) plate. We see websites, applications and emails being hacked to retrieve sensitive information pertaining to an individual or a company. Ever wondered why emerging or established companies fall prey to such attacks performed by hackers? One of the main reasons is poor investment in security measures.
So what is IT Security all about and what wonders does it play against these hackers? IT security is all about protecting a system to its lengths and breadths. Cyber security focuses on protecting networks, computers, servers and applications along with detection and prevention of unauthorized access from alteration and/or destruction of data.
Threats encountered in 2014- To show you an example of how external hacking threats can hamper an organization, here are some notable events in 2014.
- Heartbleed bug – The Heartbleed bug was detected back in April, 2014. It exposed vulnerabilities in the OpenSSL cryptography software library, further affecting many websites.
- Shellshock – Shellshock was discovered in September 2014, as it allowed hackers to run malicious scripts in systems and servers, further compromising data stored for confidential purposes.
- Sony Pictures – The Sony Hack was one of the major attacks as it displayed a threatening message on every screen present on its network. The threat was conducted by Guardians of Peace (GOP), a cyber hacking team. They also exposed sensitive data (passwords, emails, personal information) by uploading them on the internet.
The need for IT Security– The threats mentioned above certainly qualify for the need of a world class security system which can not only detect threats but also have the capacity to withstand and defend the system in all situations. When we discuss situations – it can be those times where a power failure can degrade the overall functioning of the security system, eventually, falling prey to hackers. It should be like the Duke protecting the fortress at all costs. His army can withstand rough weather, indefinite attacks from enemies, from all sides of the fortress. As dead ammunition does not add weight on the battlefield and exposes loopholes in the attack strategy, similarly, having poor security system may not provide any resistance and may trigger failure during an attack.
Tools of IT Security – We all rely on basic tools given in the computer’s onboard operating system for protecting the system from external threats. Well, these features may be minimalistic but can save you from losing sensitive and valuable data stored on your computer. Antivirus, Firewall, DMZ, Malware Protection, etc, are some of the tools that can brief up your system against external threats. However, it is important to keep these tools active and updated to enable round the clock protection.
Techniques of IT Security: To begin with, here are some techniques of IT Security which are used across the globe.
- Application Security Testing – Security Testing helps in identifying security flaws in an application. A comprehensive Application Security Testing policy can surely protect and enhance the functioning of the application, leaving it free from hackers. There are others in the list of IT Security which include:
- Threat modeling – The dynamics of the application architecture are checked to identify the loopholes in application design. Identified vulnerabilities are rated and grouped to segregate the type of threats that can cause damage to the application. Application scanning and security – In Application Scanning and Security, automated and manual testing methods are improvised to identify the vulnerabilities categorizing as SQL Injection, Cross Site Scripting, Parameter Manipulation, etc. These tried and tested techniques can add practicality to the armament.
- Cloud Security – Many cyber security companies offer various types of security policies for their clients and ensure smooth access to data stored in cloud. Cloud security is booming lately because of the host of services it offers for an affordable price. Several startups are moving to cloud security for long-term benefits.
- Infrastructure security assessment – Hosting environments which include app servers, web servers, and networks are identified for any sort of threats. Adherence of HIPAA guidelines can be improvised for Infrastructure security assessment, further increasing the chances of alerting and squaring the attack for zero percentage damage.
- Security audit – A security audit performs testing at a rigorous level to know the problems in an application or system. A comprehensive review is done to understand and highlight the entry points for a threat. Failing to perform an immediate action where required can increase the chances of data theft or destruction.
In the above mentioned techniques, it is equally important to test and upgrade the current systems as per the requirements. Testing plays an important role in identifying errors which might appear during the initial scanning of threats. It clearly supports the phrase “A chain is only strong as its weakest link”. Monthly assessments of security tools is equally a necessity to understand if there are any new threats lurking in the system, be it internal or external. Many organizations adhere to penetration testing as a result of finding faults in the system, further rectifying it to be 100% defensive against alarming threats.
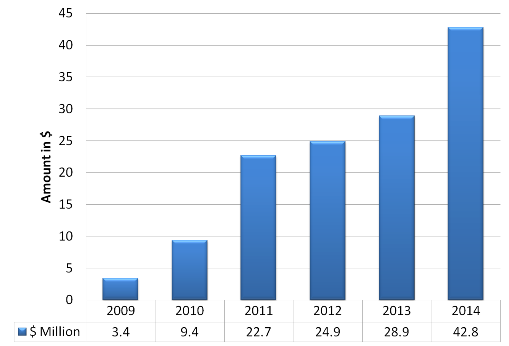
As per PWC, we can see the graph which portrays the damages caused by having poor/weak security from the year 2009 to 2014. The amounts show an upward trend almost shooting up to $43 million. In an industry where everything is recorded and saved online, it raises a concern for new entrants eventually prioritizing them to invest in top of the class security.
By the reports we see, it is quite evident that in these testing times it is important to have the mentioned techniques utilized for IT Security. With these updates and developments in the IT Security sector, we can surely expect the protection of valuable and sensitive information at the highest level.